Recently while setting up a new Fortinet FortiGate firewall High Availability (HA) pair, I ran into an issue that I hadn’t encountered before. The goal was to set up an active/standby HA pair and having done this many times, didn’t think much of it when configuring the normal HA settings...
For this article I will use my lab unit. (the firewalls I was configuring had HA settings similar to this):
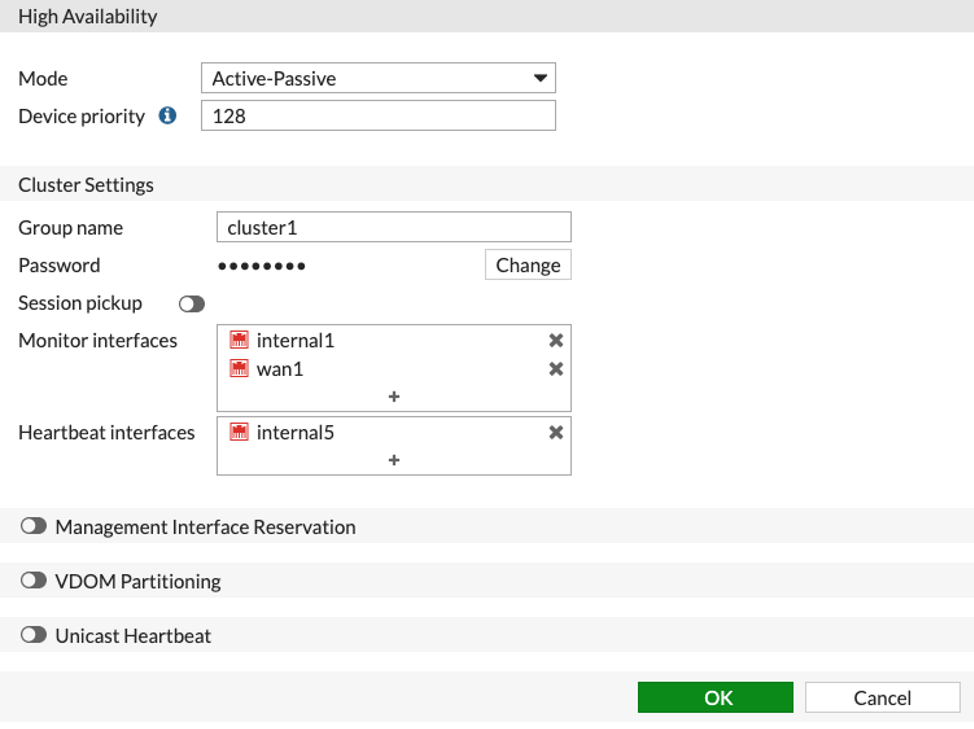
While configuring HA, I clicked “OK” to save my changes and then the unexpected happened: I lost all connectivity to the Fortigates that I was staging. I did some troubleshooting and noticed MAC flaps on the upstream switches facing the Fortigate as soon as HA was enabled. I rolled back the HA changes which restored access to the Fortigates I was staging.
After doing some research I stumbled upon this Fortinet knowledge base article:
https://kb.fortinet.com/kb/documentLink.do?externalID=11772
It says that by default when you enable HA on Fortigate firewalls, the same MAC address on each interface will be used regardless of platform. By default interface MAC addresses will become the following values:
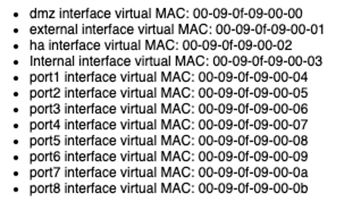
So that begs the question: What if you have 2 high-availability pairs on the same network? Well in my case you will have MAC address flaps on your switches and will lose connectivity to your HA pair and possibly cause a network outage.
After doing some research I found another document where under the HA settings you can add a configuration called “group-id” but this must be entered from the command line, it’s not available in the web interface. What this does is convert the ID number you give it from decimal format into hexadecimal and use this value as the 5th octet of each interface on the firewall HA pair.
Here is the configuration with HA enable but with the default group id:
config system ha
set group-name "cluster1"
set mode a-p
set password ENC My_Password_Hash
set hbdev "internal5" 0
set override disable
set monitor "internal1" "wan1"
end
If we look at the DMZ interface we see that it is using the default HA MAC address:
FGT60D_Lab (global) # diagnose hardware deviceinfo nic dmz | grep HWaddr
Current_HWaddr 00:09:0f:09:00:00
Permanent_HWaddr 08:5b:0e:4c:ac:db
We see the default DMZ MAC address as expected.
Let’s modify the group-id and see what happens:
config system ha
set group-id 30
set group-name "cluster1"
set mode a-p
set password ENC My_Password_Hash
set hbdev "internal5" 0
set override disable
set monitor "internal1" "wan1"
end
30 as hexadecimal is 1e so let’s check:
FGT60D_Lab (global) # diagnose hardware deviceinfo nic dmz | grep HWaddr
Current_HWaddr 00:09:0f:09:1e:00
Permanent_HWaddr 08:5b:0e:4c:ac:db
As you can see the 5th octet of the interface MAC address has been updated to the hexadecimal value of 30 as expected. Once this has been changed we are now able to have both Fortigate HA pairs exist on the same network without issue.
In summary, I feel that this method for determining the MAC addresses used in an HA pair has some room for improvement. But for now this is how it works so we should always be sure to set the “group-id” on an HA pair to something unique in order to avoid issues with MAC address conflicts when there are multiple Fortinet FortiGate HA pairs on your network.
Thanks for reading! Please send any questions, comments or other to info@wandynamics.com.

